For this assignment our class was tasked with collecting packet data with the Wireshark tool. I chose to run Wireshark on my home network while running YouTube, Authy, Notion, ProtonMail Client, and Spotify on my laptop, Netflix on my iPad, and texting friends on my phone, for an hour. For half of that time I ran my Mullvad VPN on my laptop using the WireGuard protocol – this was apparent in my packet results. I used the MaxMind GeoLite 2 plugin to make my packet data more legible. In all, I captured 128926 packets.
Expectations:
1. In a previous assignment for Harlo Holmes’ Digital Security and Human Rights class, we had analyzed a day’s worth of packets from our personal computers. I recall capturing evidence that specific components in my laptop were transmitting packets to China. However, I could not find evidence of this occurrence this time – I think this is because I could not find the specific tool that Harlo provided us to make Wireshark data more legibile.
2. In the same assignment for Digital Security and Human Rights, I discovered that the application Notion would intermittently send HTTP requests to what we presumed was the company. Overall I had 3501 HTTP request packets (0.7%), with almost 90% NOTIFY requests, 9% SEARCH requests, and 1% GET requests. It is my understanding that in addition to Notion, which I identified through traceroute of some HTTP packet IP addresses and a Google search, other applications engaged in the same activity. Again, I am confident that my insights would be more legible with Harlo’s tool.
3. I anticipated specific requests on the ports 1025 and 1143, the STMP and IMAP ports for ProtonMail’s security client. When I searched my packet results, I found no activity on these ports and was confused by this.
Analysis
With the MaxMind GeoLite2 tool I was able to get an HTML visualization of my endpoint traffic geography. Below I will display the images for my Ipv4, TCP, and UDP packets. As was the case in our traceroute assignment, it should be noted that the geographic accuracy of these results are limited, as addresses with nondescript entity registration will be represented more centrally in a given state or country on a map.
Ipv4
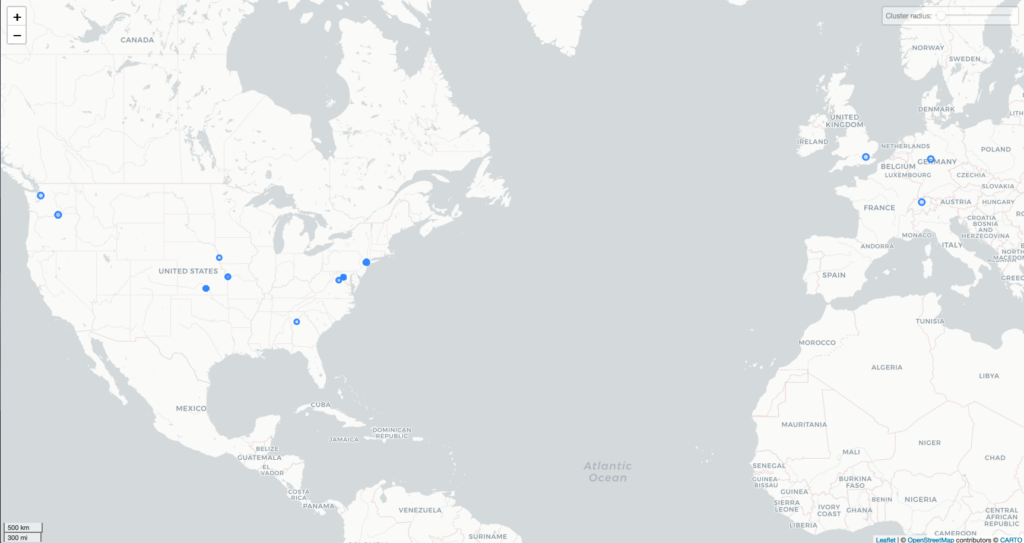
I found evidence of the following companies: Dropbox, Fastly, Amazon, Microsoft, Google, and Hertzner Online. What set this map apart was the activity in Atlanta, by the company Performive, which I initially attributed to my VPN, but I now attribute to my roommate’s virtual environment software for his job. I was most displeased to see the presence of Barefruit LTD in the UK, a company that claims to monetize HTTP and DNS errors, supplanting them with “relevant advertisement at the network level” – essentially a company that suggests alternative pages to links that are broken.
TCP
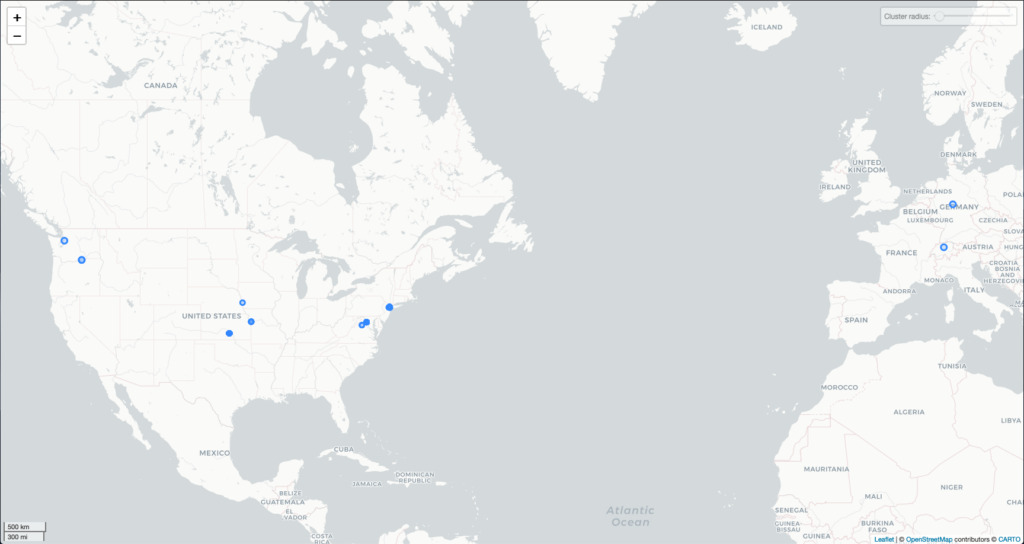
Without further investigation I cannot corroborate this, but in New Jersey, I saw evidence that Apple Engineering was receiving packets. Perhaps this was evidence that my computer components were “talking” to Apple, transmitting whatever analytics the company collects. Whatever Apple collects, they do so in high volume, as that IP address had nearly 20,000 packets transmitted to them. I also found evidence of TCP packet transmission to Proton Technologies (Protonmail), which must have been sent on the more secure port 443 instead of the ports that I anticipated. Other revealed companies include Dropbox, Fastly, Amazon, Microsoft, Google (clustered in central United States), and Hertzner Online. After seeing Hertzner Online for the second time, I investigated, and found that it was a VPN service, presumably the one that my roommate’s company uses.
UDP
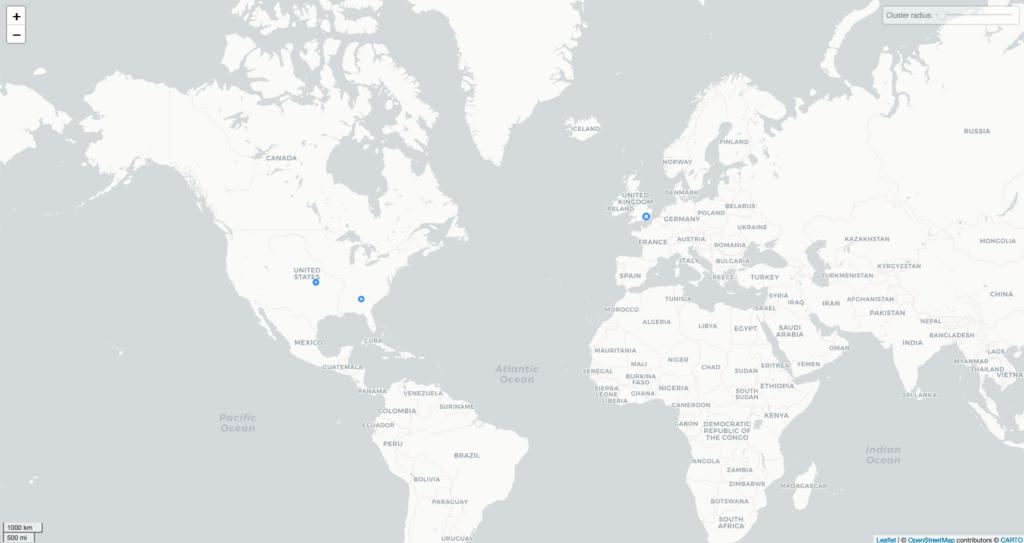
I presume that my UDP IP addresses were obfuscated to some degree, because I was streaming on a bunch of video platforms (videos use the UDP protocol for packet transmission because it can operate with a certain degree of packet loss). The only companies that showed up were Google, Performive, and (unfortunately) Barefruit.
Inbound and Outbound
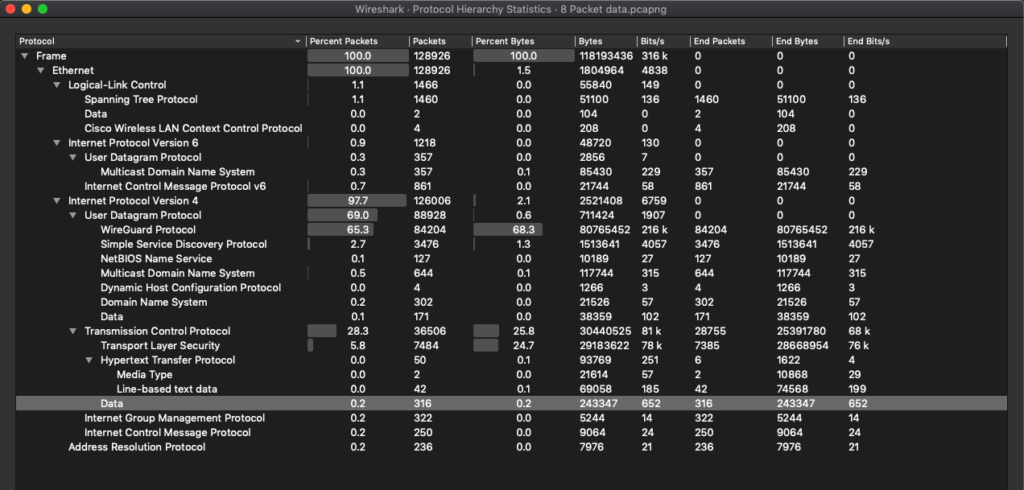
There were 39 unique device conversations that occurred on my network. I discovered this by looking at the Ethernet tab (which displays mac addresses) within the conversation statistics tool on Wireshark. I counted 12 unique wifi capable devices on my network – not all of which I can account for, in part because I didn’t want to bother my roommate to see what his mac addresses were. The chattiest and best listening device was my laptop, which received 109 million packets and transmitted 87,092 packets. My iphone and ipad were silent by comparison, receiving only a couple of thousand packets each, barely transmitting at all. Over UDP, TCP, and Ipv4, protocols my devices talked more than they listened, at their greatest by a factor of 1 million. Below is a summary of the different protocols used in my Wireshark capture, and their prevalence.
Traceroute Roadblocks
I tried to traceroute some IP addresses that my computer engaged with most frequently over TCP and UDP. Even when I conducted traceroutes specific to the ports that Wireshark revealed, when I analyzed my results in MaxMind’s GeoIP tool I often bumped up against the following error:
“the IP address ‘XX.XX.X.X’ is a reserved IP address (private, multicast, etc.)”
Ipv6 for my Router
I noticed that my router would intermittently conduct multicast listeners and reports using both the Ipv6 protocol and Spanning Tree Protocol in order to discern which devices were on my network. Fun fact, I have an Arcadyan brand router apparently.
Moving Forward
I need to follow up with Harlo to figure out what tool she gave us for Wireshark. I’d like to talk to Tom Igoe about why I did not see port activity specific to ProtonMail. I will also follow up with my roommate to see if I can identify all of my wifi-capable devices.